Notepad++ patches hijacked updater after targeted supply chain compromise
Attackers hijacked Notepad++’s legacy update system to deliver a backdoor to a small set of users; as few as a dozen machines may have been targeted.
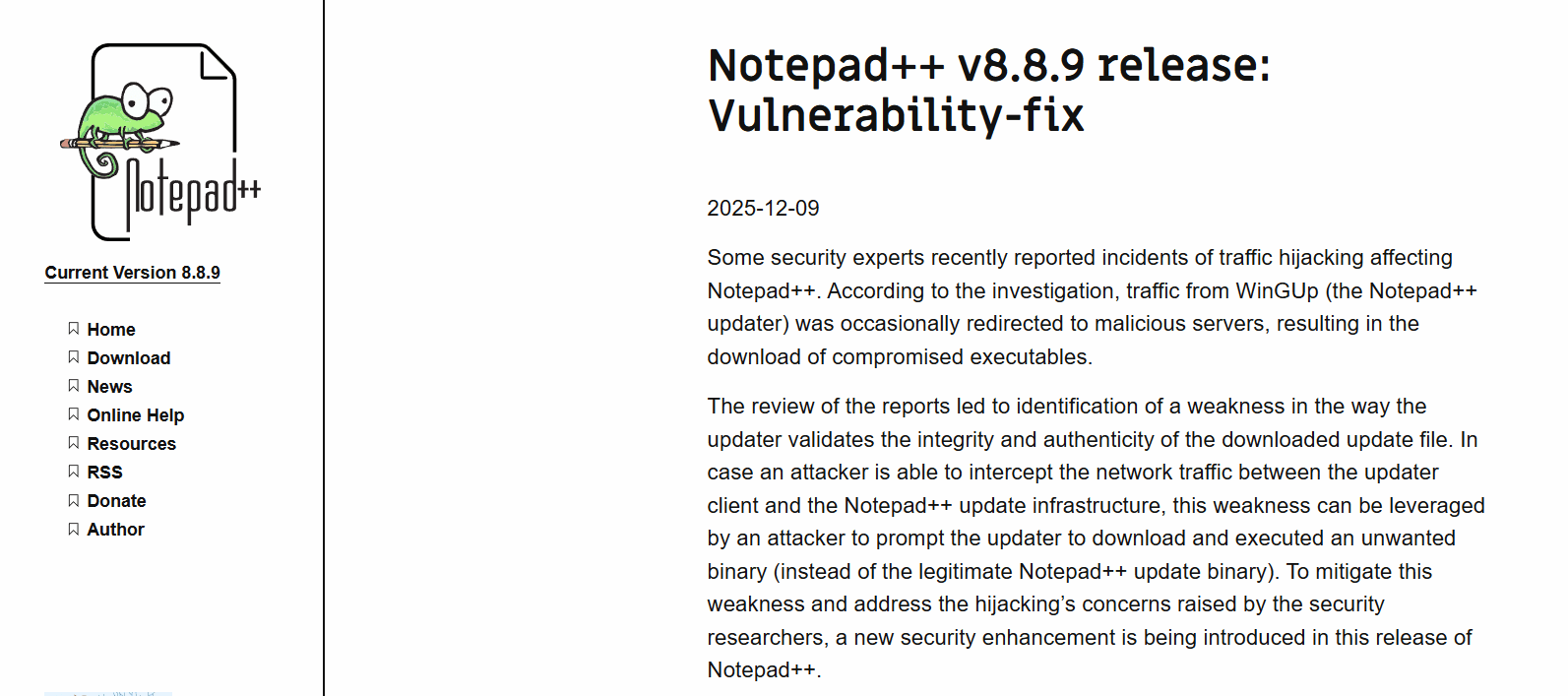
Attackers hijacked Notepad++’s legacy auto-update mechanism to push malicious installers to a small, highly targeted set of users between June and December 2025, security researchers and the project maintainer confirmed. Investigators say most users continued to receive legitimate updates, but Kaspersky’s analysis suggests as few as a dozen individual machines were specifically targeted.
The intrusion stemmed from an infrastructure compromise at a third-party shared hosting provider used by Notepad++’s legacy WinGUp updater. When vulnerable clients checked for updates, WinGUp contacted the endpoint notepad-plus-plus.org/update/getDownloadUrl.php. Attackers who controlled the hosting infrastructure were able to intercept those requests for selected targets, redirect them to attacker-controlled servers, and return update manifests that pointed to trojanized installers. Under the legacy workflow, WinGUp downloaded and executed the supplied binaries without strong signature validation, enabling code execution at user privilege levels.
Notepad++’s advisory on the incident summarized the finding: "According to the analysis provided by the security experts, the attack involved infrastructure-level compromise that allowed malicious actors to intercept and redirect update traffic destined for notepad-plus-plus.org. The exact technical mechanism remains under investigation, though the compromise occured at the hosting provider level rather than through vulnerabilities in Notepad++ code itself. Traffic from certain targeted users was selectively redirected to attacker-controlled served malicious update manifests."
Rapid7 and Kaspersky analysts reported that tampered updates delivered a previously undocumented backdoor dubbed Chrysalis. Multiple reporting links the campaign to a China-linked state actor; names used in different analyses include Lotus Panda and Lotus Blossom. Because attribution labels vary across analysts, researchers urge caution and further corroboration before assigning definitive responsibility.
The operation exploited a weakness in update integrity validation in the WinGUp updater tracked in some reports as CVE-2025-15556, which has a reported CVSS score of 7.7. An additional high-severity flaw addressed in the emergency updates, CVE-2026-25926, is described as an Unsafe Search Path issue with a reported CVSS score of 7.3. Security teams recommend confirming the CVE entries and scores in official vulnerability databases before relying on the specific metrics.
Notepad++ issued patched builds that strengthen signing and verification of update files; reporting names version 8.9.1 as the immediate fix and some sources recommend updating to 8.9.2. Users who manually downloaded installers from the official Notepad++ website or GitHub releases were not affected. Administrators are advised to update manually, audit systems that ran in-app updates between June and December 2025, rotate exposed credentials, and review logs for signs of compromise.
The hosting provider moved affected customers to new servers, fixed the vulnerabilities that had been abused, rotated exposed credentials, and reviewed system logs, concluding there was no evidence of continued attacker access after remediation. Notepad++ maintainers have said there is no evidence the project’s source code, developers, or build environment were compromised.
This episode underscores the persistent danger of supply chain attacks that do not touch application code but instead exploit update delivery infrastructure and weak verification controls. Past incidents in the software supply chain show similar tradecraft, and defenders are left with a narrow set of mitigations: enforce cryptographic signing of updates, retire legacy updaters like WinGUp, and treat shared hosting credentials and update endpoints as crown-jewel infrastructure.
Know something we missed? Have a correction or additional information?
Submit a Tip